The next step is to generate your Client Assertion.
You can use any online jwt tool for this e.g - https://dinochiesa.github.io/jwt/.
- In the Decoded Header section, you put in the following json:
{
"alg": "RS256",
"typ": "JWT"
}
- In the Decoded Payload, you put in the following json and replace the placeholders with your own information:
{
"iss": "{{Company Url}}",
"sub": "{{OAuth Client ID}}",
"aud": "{{Safe Haven Environment}}",
"iat": "{{Issued At}}",
"exp": "{{Expiry}}"
}
Company Url: Your Company URL
OAuth Client ID: Can be gotten from Safe Haven Dashboard
Safe Haven Environment: This is https://api.safehavenmfb.com ( for Production) and https://api.sandbox.safehavenmfb.com (for Sandbox).
Issued At: This is the timestamp of the date you create the client assertion jwt. You can generate a timestamp using https://www.epochconverter.com/.
Expiry: This is the timestamp of the date you want the client assertion jwt to expire.
Note: The timestamp's format should look like this – "1639806203".
- In this example, the client assertion is generated using https://dinochiesa.github.io/jwt/. In the Private Key Section, paste the private key you generated earlier when creating your app on the Safe Haven dashboard and leave the public key section empty.
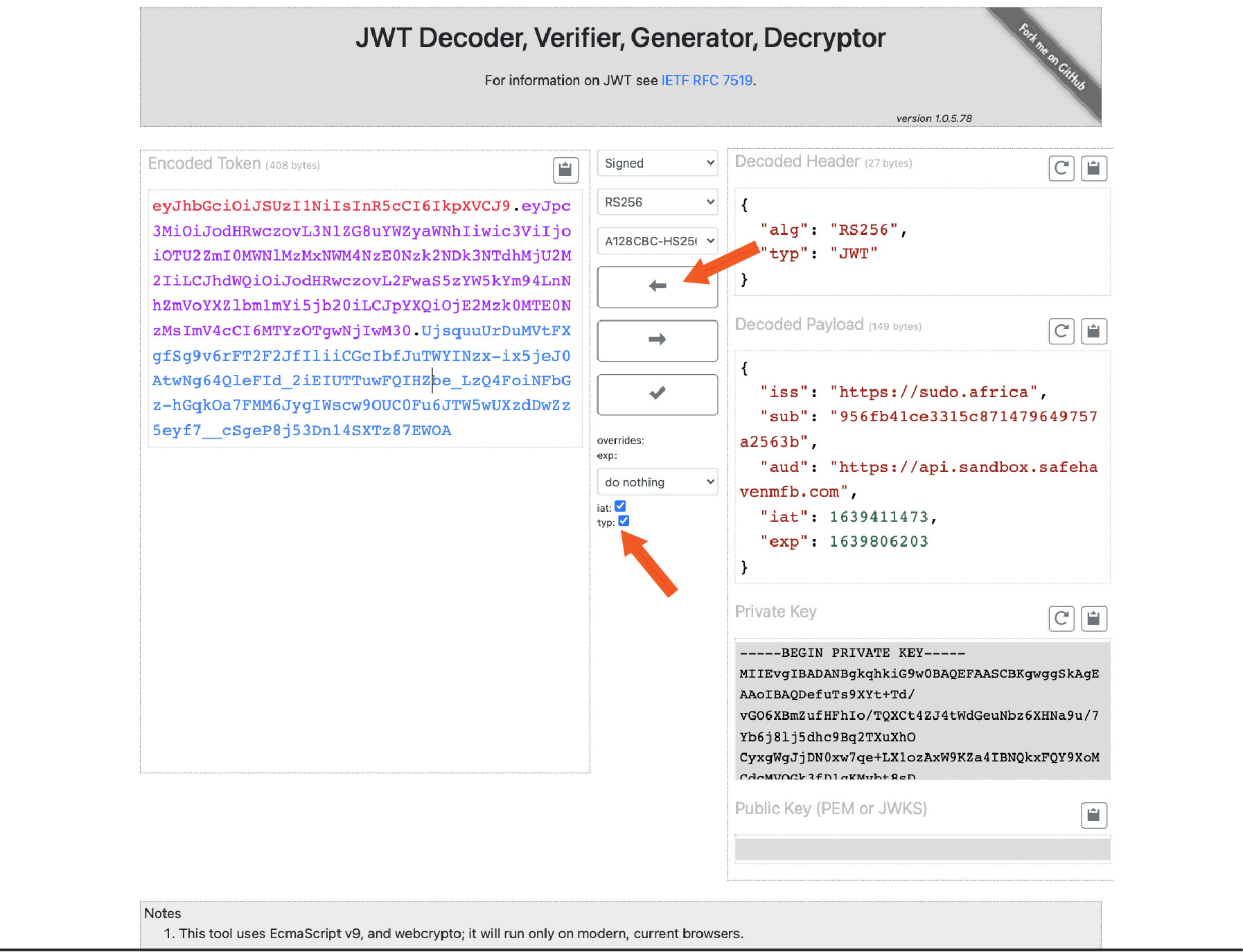
Ensure to tick the 'iat' and 'typ' boxes and click on the arrow button facing left to encode it and generate your client assertion.
Next Step:
The next step would be to generate your access token using the client assertion generated above. Click here to take you to the endpoint to generate your access token.